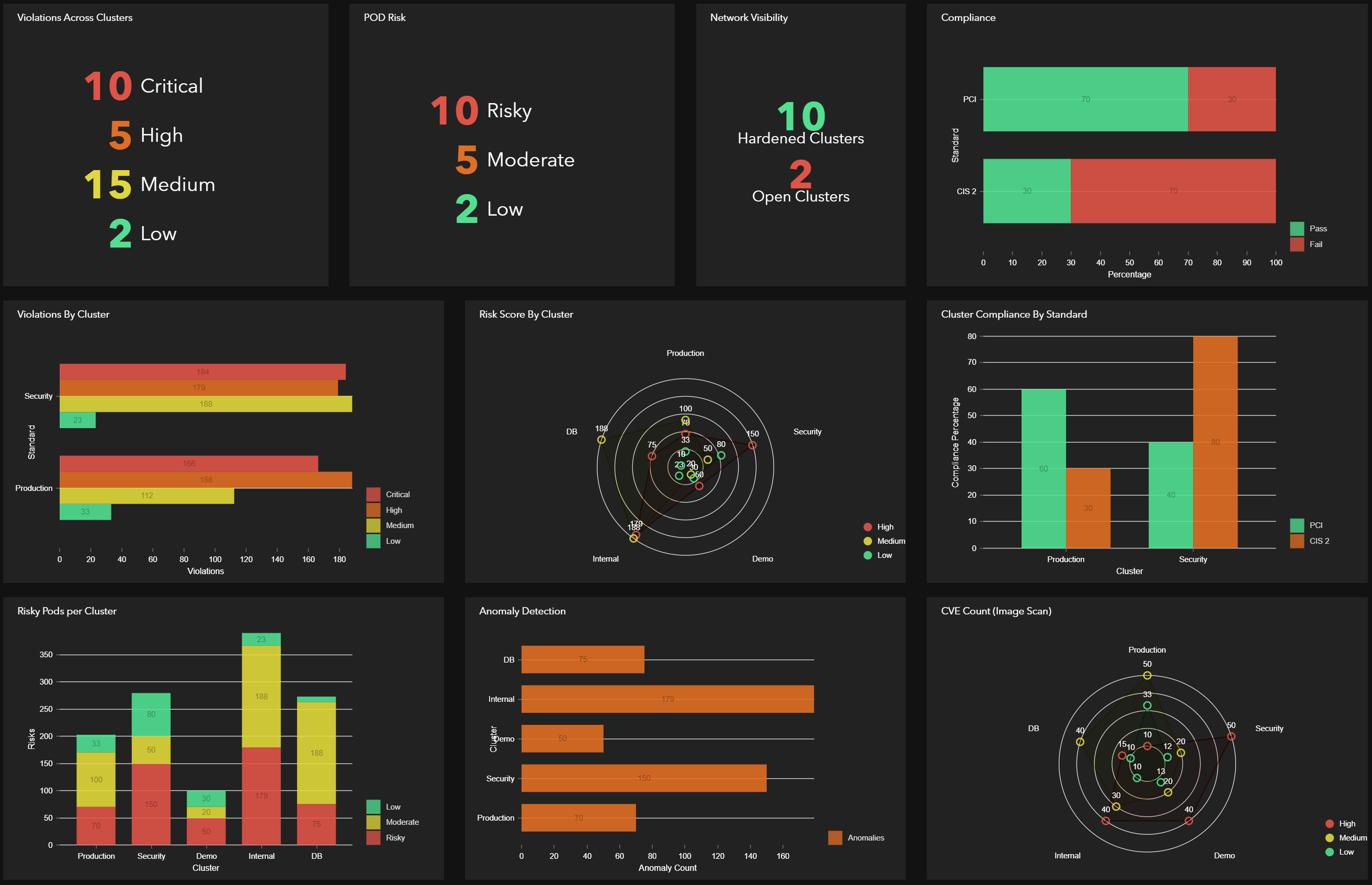
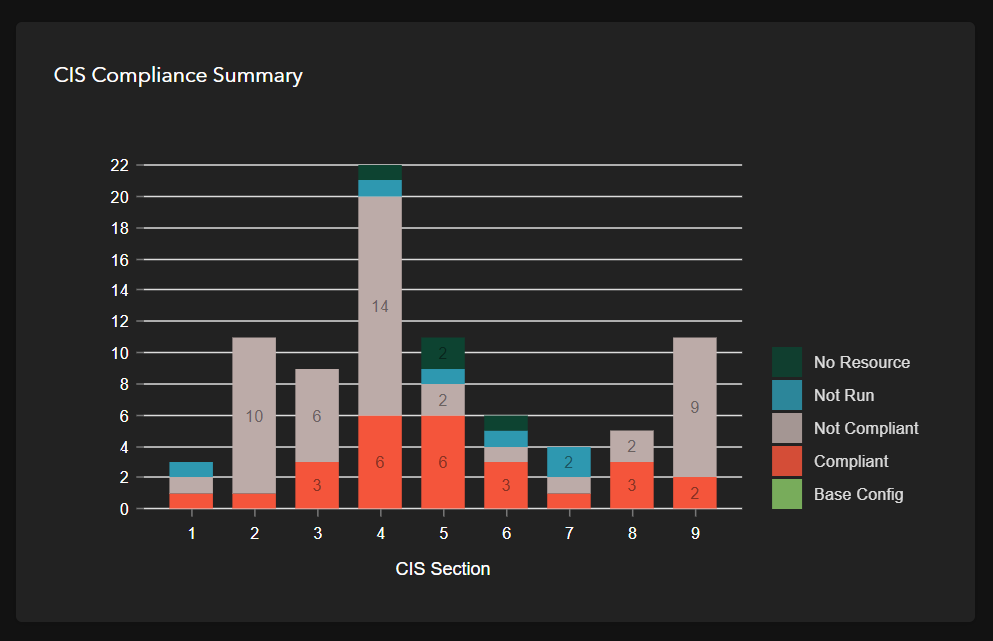
Protect Your Data
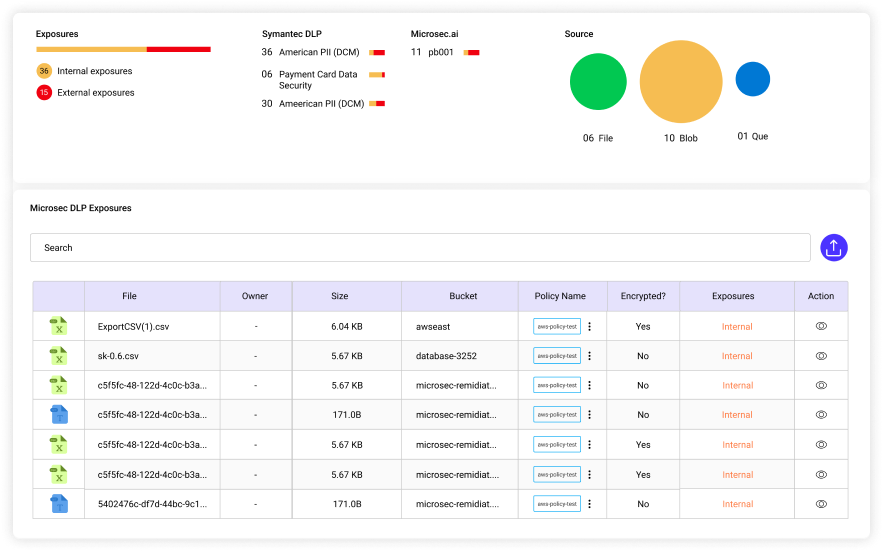
- Data classification at-rest/in-motion
- Enterprise DLP integration
- East-west data detection and control
- Exposure analysis and remediation
- Encryption status
PROTECT APPS IN RUNTIME
- Intrusion detection
- VM & container security
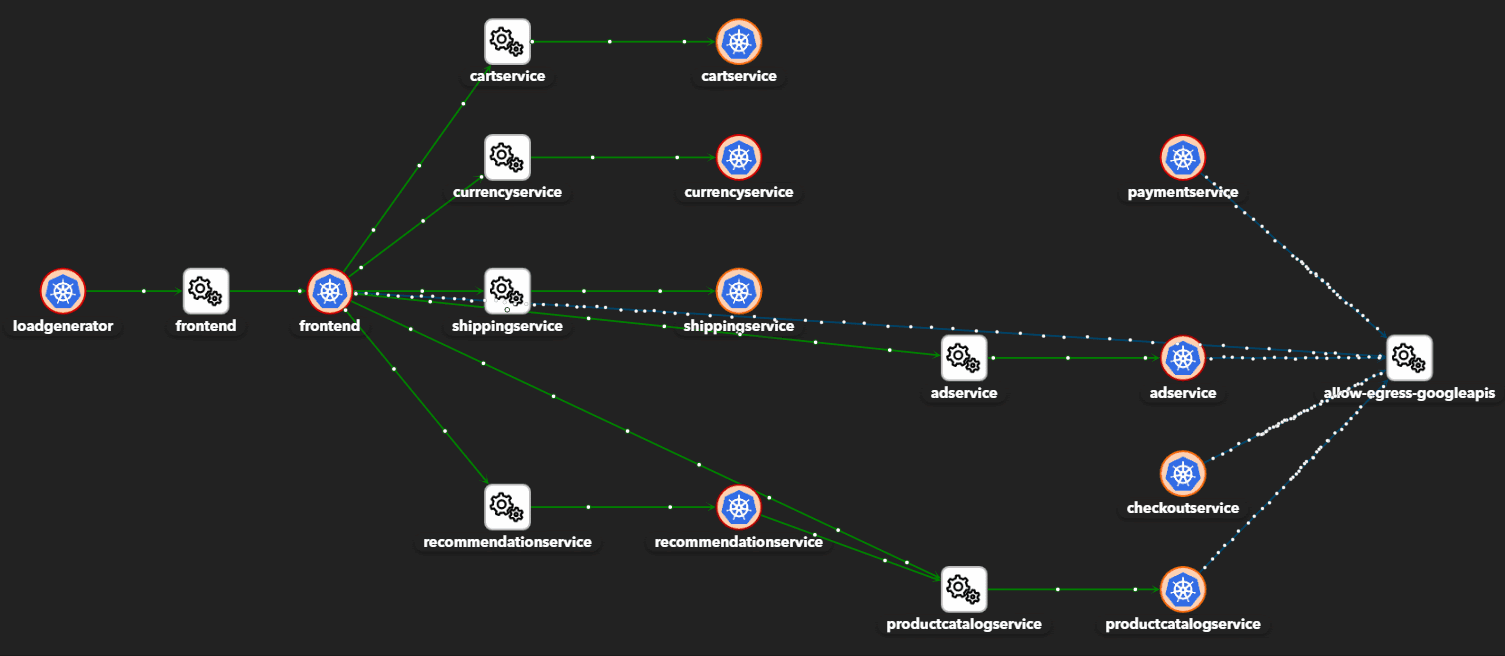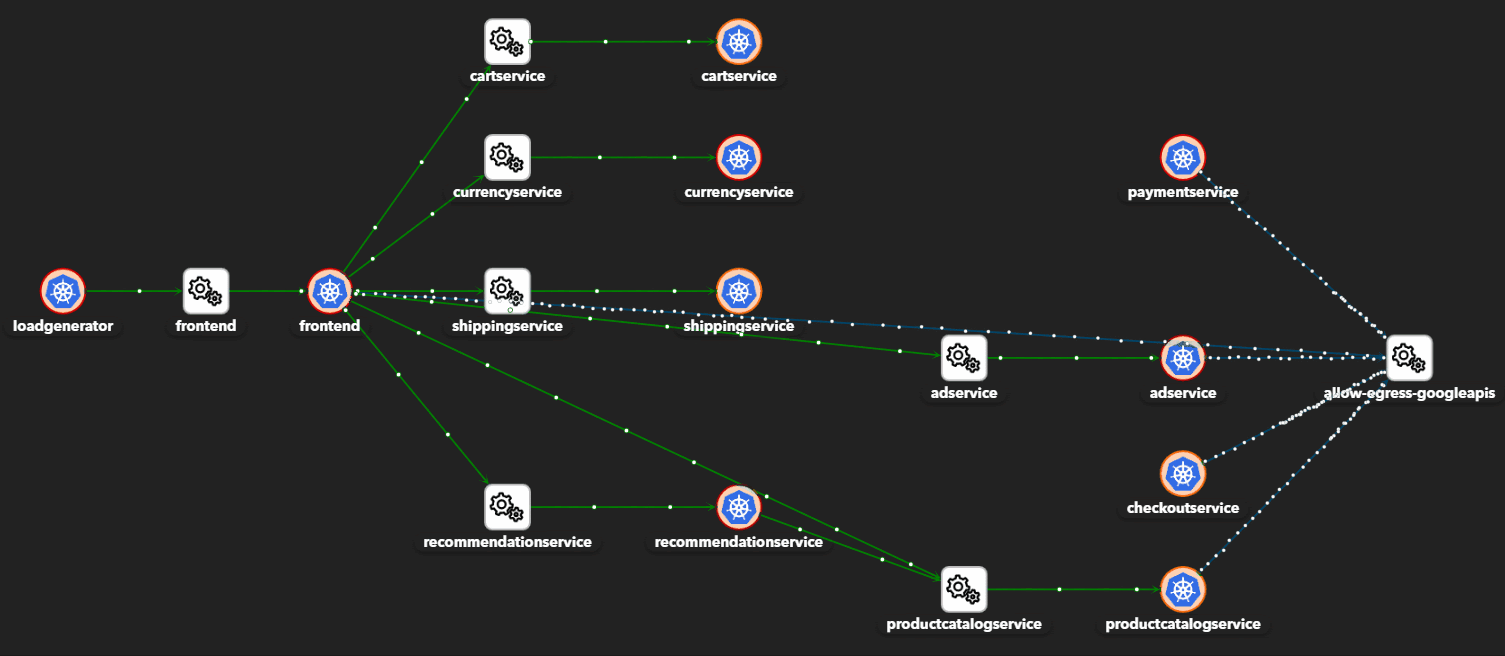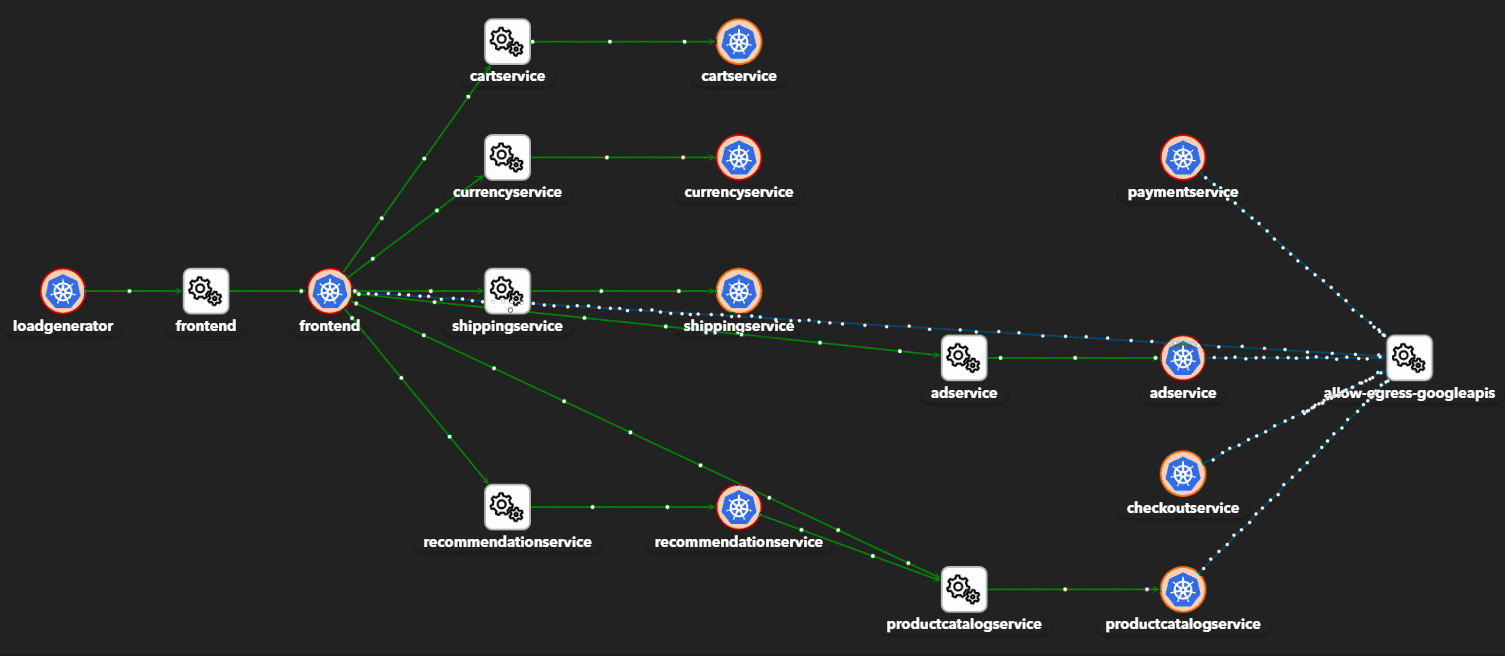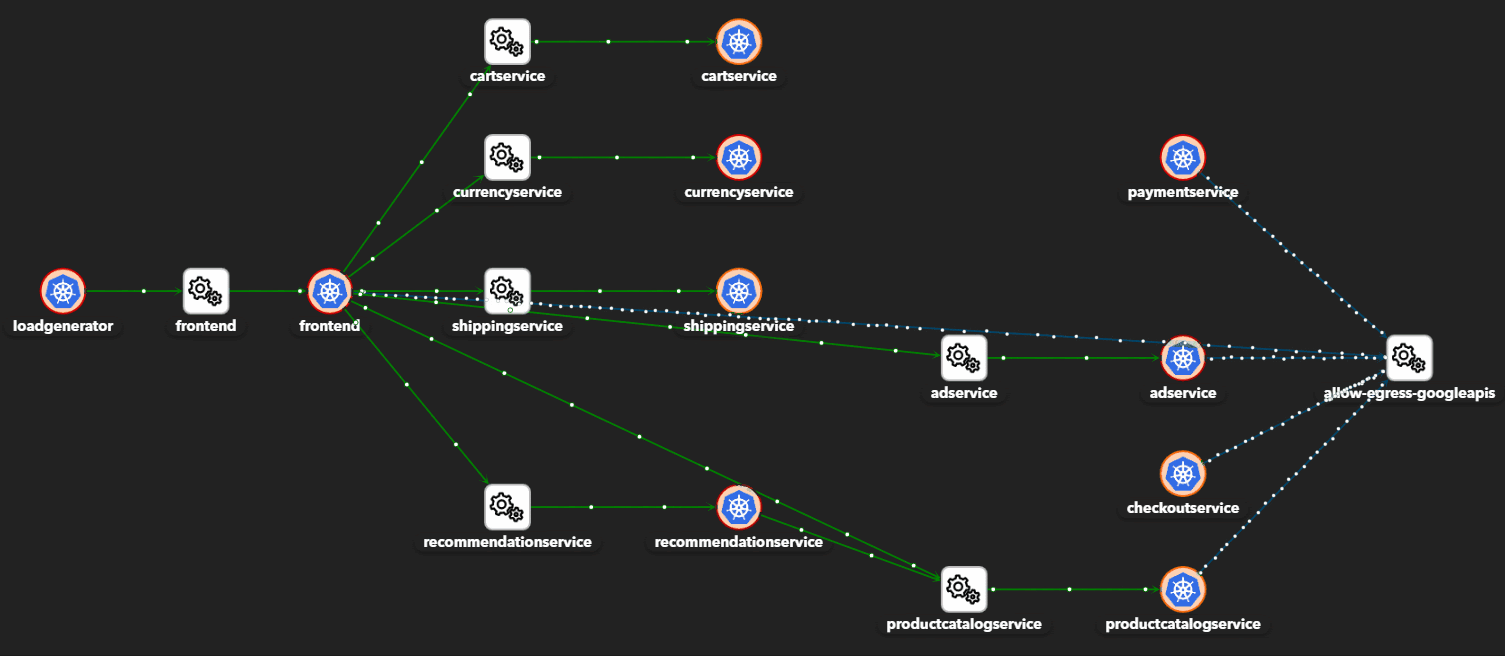
- Application and network visibility
- Threat investigations & resolution
- Adaptive east-west microsegmentation